What exactly is an unmanaged VPS?
Before we move to the security checklist, let’s find out exactly what an unmanaged VPS is and what benefits it can bring to you. With an unmanaged VPS, pretty much everything will be your responsibility. Once the initial setup is complete, you will have to take care of server maintenance procedures, OS updates, software installations, etc. Data backups should be within your circle of competence as well. This means that you will need to have a thorough knowledge of the Linux OS. What’s more, you will have to handle any and all resource usage, software configuration and server performance issues. Your host will only look into network- and hardware-related problems.Why an unmanaged VPS?
The key advantages of unmanaged VPSs over managed VPSs are as follows:- you will have full administrative power and no one else will be able to access your information;
- you will have full control over the bandwidth, storage space and memory usage;
- you will be able to customize the server to your needs specifically;
- you will be able to install any software you want;
- you will save some money on server management – it really isn’t that hard to set up and secure a server if you apply yourself and updating packages is very easy;
- you will be able to manage your server in a cost-efficient way without the need to buy the physical machine itself (you would have to if you had a dedicated server);
Unmanaged VPS – security checklist
With an unmanaged VPS, you will need to take care of your sensitive personal data. Here is a list of the security measures that our administrators think are key to ensuring your server’s and your data’s health: 1. Use a strong password Choosing a strong password is critical to securing your server. With a good password, you can minimize your exposure to brute-force attacks. Security specialists recommend that your password be at least 10 characters long. Plus, it should contain a mix of lower and uppercase letters, numbers and special characters and should not include common words or personally identifiable information. You are strongly advised to use a unique password so as to avoid a compromised service-connected breakthrough. A strong password may consist of phrases, acronyms, nicknames, shortcuts and even emoticons. Examples include:
1tsrAIn1NGcts&DGS!:-) (It’s raining cats and dogs!)
humTdumt$@t0nAwa11:-0 (Humpty Dumpty sat on a wall)
p@$$GOandCLCt$500 :-> (Pass Go and collect $500)
2. Change the default SSH port
Modifying the default SSH port is a must-do security measure.
You can do that in a few quick steps:
- Connect to your server using SSH
- Switch to the root user
- Run the following command: vi /etc/ssh/sshd_config
- Locate the following line: # Port 22
- Remove # and replace 22 with another port number
- Restart the sshd service by running the following command: service sshd restart
- Create the user by replacing example_user with your desired username (in our case – ‘admin’):
adduser admin - Set the password for the admin user account:
passwd admin - To get admin privileges, use the following command:
echo 'admin ALL=(ALL) ALL' >> /etc/sudoers - Disconnect and log back in as the new user:
ssh admin@my.ip.or.hostname - Once you are logged in, switch to the root user using the ‘su’ command:
supassword:whoamiroot - To disable the root user login, edit the /etc/ssh/sshd_config file. You will only need to change this line:
#PermitRootLogin yesto:PermitRootLogin no
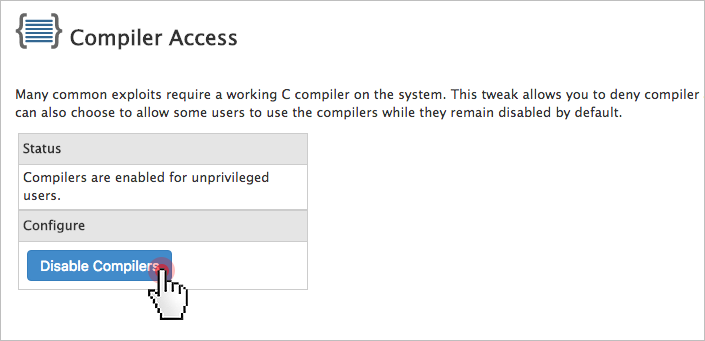


apt-get install libapache2-modsecurity
Here’s a quick guide on how to install and configure ModSecurity.
Once you’ve got ModSecurity up and running, you can download a rule set like CRS (OWASP ModSecurity Core Rule Set). This way you won’t have to enter the rules by yourself.
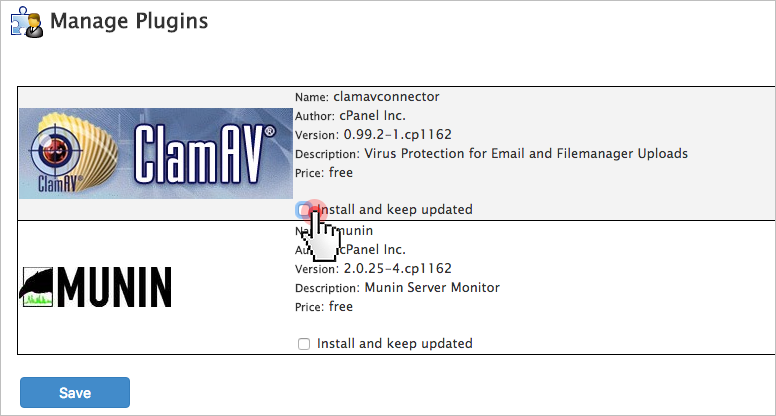
9. Set up anti-virus protection
One of the most reliable anti-virus engines is ClamAV – an open-source solution for detecting Trojans, viruses, malware & other malicious threats. The scanning reports will be sent to your email address.
ClamAV is available as a free cPanel plugin.
You can enable it from the Manage Plugins section of your WHM:

 If you are on a tight budget, you can keep your backups on your local computer.
12. Keep your software up to date
Keeping your software up to date is the single biggest security precaution you can take.
Software updates range from regular minor bug fixes to critical vulnerability patches. You can set automatic updates to save time.
However, keep in mind that automatic updates do not apply to self-compiled applications. It’s advisable to first install an update in a test environment so as to see its effect before deploying it to your live production environment.
Depending on your particular OS, you can use:
If you are on a tight budget, you can keep your backups on your local computer.
12. Keep your software up to date
Keeping your software up to date is the single biggest security precaution you can take.
Software updates range from regular minor bug fixes to critical vulnerability patches. You can set automatic updates to save time.
However, keep in mind that automatic updates do not apply to self-compiled applications. It’s advisable to first install an update in a test environment so as to see its effect before deploying it to your live production environment.
Depending on your particular OS, you can use:
- yum-cron (for CentOS)
- unattended upgrades (for Debian and Ubuntu)
- dnf-automatic (Fedora)
***
If you have not obtained an unmanaged VPS yet, you could consider our solutions:- OpenVZ VPS packages – all setups from 4 to 10 are unmanaged and come with SSH/full root access (for cPanel setups only) and with a CentOS/Debian/Ubuntu OS installation;
- KVM VPS setups – all four setups are unmanaged and offer SSH/full root access; OS options include CentOS/Debian/Ubuntu as well as a few OS ISO alternatives like Fedora and FreeBSD;



